With cyber-security threats coming from all directions, it’s important for CPA firms to be aware of how the risk exposures impact the firm as well as the client. Just as important is understanding how an effective cyber insurance program works with the firm before and after a cyber incident occurs.
Cyber exposures and coverages are basically divided along two lines:
- First-party, which refers to losses directly borne by the policyholder (or insured) firm, and
- Third-party, which refers to damages alleged by clients or other third parties for which the policyholder firm may be liable.
The line between the two may become blurred when a hacker has managed to penetrate both the firm’s and the client’s computer systems. But insurance coverages typically respond according to which party is bearing losses or alleging damages.
First-party exposures
have become increasingly problematic for CPA firms. Here are a few major reasons why:
-
- Cyber-criminals are targeting CPA firms and tax professionals with greater frequency because of the abundance of client data found on the firms’ computers. The Internal Revenue Service issued a warning to tax professionals earlier this year that data such as income, dependents, credits and deductions are ideal for helping scammers make fraudulent tax returns look legitimate. To learn more about the IRS and its security partnership, click: Security Summit.
- By inducing a recipient to click an innocent-looking link or attachment, hackers penetrate a firm’s computer system to access client data, read email messages, and commandeer email and other programs. A common scam is to change bank account and routing numbers on client tax returns so that refunds are deposited into the scammers’ bank accounts instead of the clients’ accounts. Hackers also use a firm’s tax software programs to falsify and submit tax returns that generate large tax refunds routed to the hackers’ own bank accounts.
- Ransomware attacks and demands against a CPA firm also generate losses borne by the CPA firm. Ransom demands can be expensive, and paying them does not guarantee that files encrypted by the malware will be restored. Rebuilding the firm’s previous work takes time, as information and data need to be gathered, re-entered and reconstructed. Such activity is in addition to other data breach expenses if an investigation determines that client data has been compromised, resulting in required notifications.
Third-party exposures
tend to arise when a hacker has penetrated the client’s computer system and uses the information found there to launch social engineering or phishing attacks against the firm. For example:
-
- By using client information, or by commandeering the client’s email accounts, scammers can make purported client email look legitimate and trustworthy, tricking someone at the firm into clicking an attachment or link, which then downloads a virus or malware. Once malware is downloaded, it can enable a hacker to gain remote access to the firm’s computer network, read email messages, and obtain information about other clients.
- “Spear phishing” targets a specific firm, or person within a firm, by using client information or a client email account to make fraudulent messages look legitimate. If the hacker squats in both the client’s and the firm’s email accounts, messages going back and forth between the client and the firm can be manipulated on both ends, making it extremely difficult to determine that a “man-in-the-middle” attack is in progress.
- Client data can also be mined by hackers to perpetrate large-dollar thefts. A common technique is to identify high-end clients who have given bill-paying and wire authority to firms providing business management services. A hacker posing as a client will email a request from the client’s email account for a wire transfer of funds into an account controlled by the hacker. If the account is in another country, the transferred funds are usually irretrievable.Loss Prevention Tip: Have controls in place and always confirm the legitimacy of an email message before clicking an attachment or link, or taking any action. Call for verbal confirmation, and receive confirmation by an actual phone call—not by email. Email and other electronic systems may also be compromised and unreliable in an incident. Voicemail can be hacked as well, making it just as unreliable as email.
- Scammers have also been known to use many ruses, posing as (for example):
- tax software companies recommending that tax preparers update their software,
- the user’s computer “security” system requiring a password,
- potential clients soliciting professional services, and
- the IRS asking preparers to update their e-services information, or to confirm their “security” (see the following example from the IRS of an email scam asking the recipient to click a link).
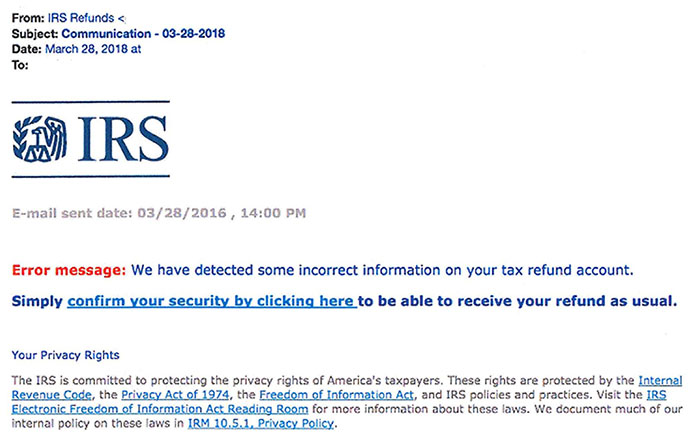
Example of an email scam, posted on the IRS website at:
www.irs.gov/pub/image/email-scam-image_1.jpg.
The IRS’s Security Summit covers the various scams used by criminals on its webpage:
Don’t Take the Bait).
Loss Prevention Tip: If an email message asks the recipient to click a link or attachment, go directly to the website for information rather than clicking on links provided in the message, or call for confirmation that the email is legitimate and not a scam.
First-Party Cyber Coverage
In the event a firm’s computer system appears to have been breached by malware, a mobile device goes missing, or anything appears to have compromised the firm’s data security, a number of steps need to be taken. A complete cyber insurance program will coordinate these steps and may provide coverage for some or all of the related expenses. Examples include:
- Investigation – The cyber risk adviser or attorney with the cyber insurance carrier coordinates an investigation to verify whether the incident is a breach as defined by current state and/or federal laws.
- IT forensics – An IT forensics expert investigates the incident as part of determining whether or not there was a security breach and if client confidential information was accessed. IT forensics experts also respond to ransomware events to assist in decrypting and restoring files as well as eradicating malware from the system.
- Notification letters – If the incident is determined to be a breach, counsel may be appointed to investigate the need for, and preparation of, notification letters to clients.
- Call centers – Clients who receive notification letters may have additional questions about the breach, and a call center will initially handle those questions.
- Credit monitoring services – Clients may demand such services in a post-breach environment.
- Public relations – PR firms may be hired in such situations to help protect the firm’s reputation. If state laws require law enforcement to be notified in the event of a theft, media reports may affect the firm’s public image and reputation.
Such losses incurred by the insured firm are generally considered “first-party” and subject to the first-party policies or endorsements.
Third-Party Cyber Coverage
If a client alleges damages arising from an insured firm’s act, error or omission, for which the insured may be liable, the damages typically would be addressed under third-party coverage included in the Accountants Professional Liability (APL) insurance policies—not the CPA’s first-party cyber coverage.
In the cyber area, one common example is the fraudulent wire transfer executed as a result of a hacker hijacking the client’s email account and prompting the CPA firm to transfer client funds into an account controlled by the hacker. Claims sometimes carry substantial third-party exposure, and once funds are transferred, they are usually not recoverable.
CAMICO includes third-party cyber coverage in its APL policy, including damages caused by fraud, social engineering, phishing, and other forms of misrepresentation. CPA firms should be wary of any APL policy that carries an exclusion for claims arising from such damages.
An information security program, including an incident response plan (IRP), should be in place to satisfy provisions of state and federal regulations. Some state regulations require such programs to be in writing. An IRP has many benefits, not the least of which is that it will help a firm use its resources wisely and efficiently to plan for a breach and thus reduce firm expenses when a breach occurs.
The information provided in this article is a general overview and not intended to be a complete description of all applicable terms and conditions of coverage. Actual coverages and risk management services and resources may vary and are subject to policy provisions as issued. Coverage and risk management services may vary and are provided by CAMICO and/or through its partners and subsidiaries.
